Introduction:
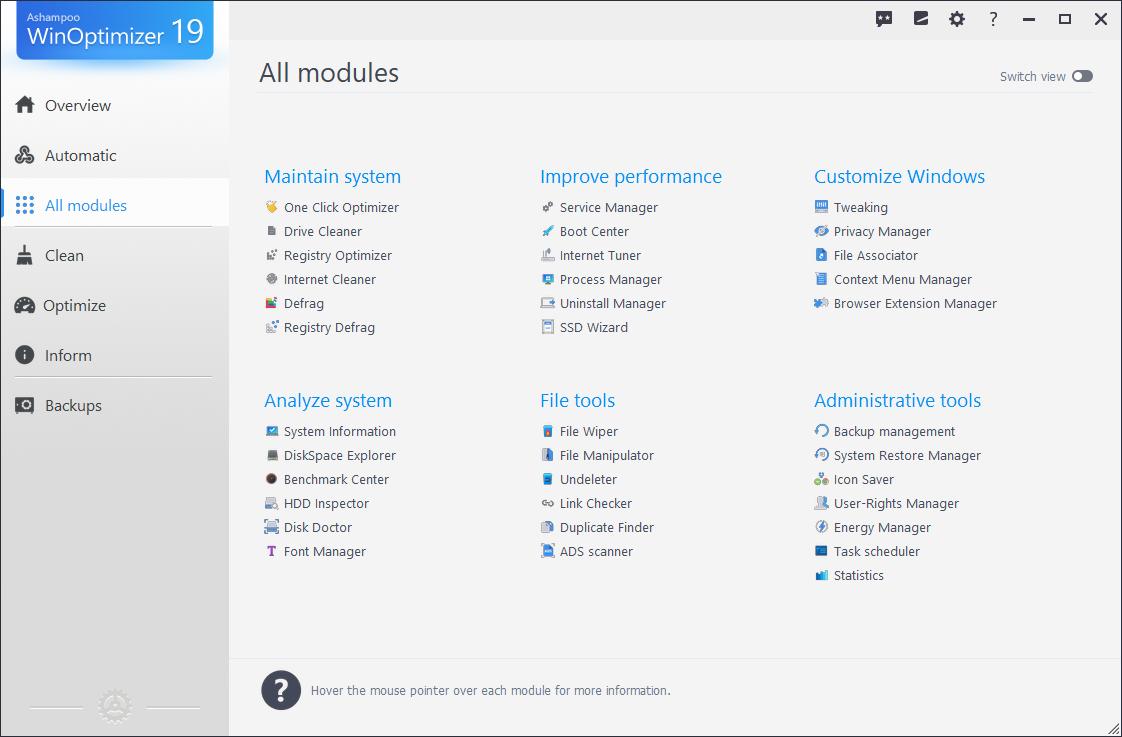
Ashampoo WinOptimizer is a powerful optimization software designed to enhance the performance of your computer while keeping your system clean and efficient. Targeted mainly at everyday users who seek to improve their PC's speed and reliability, it is recognized as one of the top choices in system optimization solutions. With its intuitive interface and comprehensive features, Ashampoo WinOptimizer ensures that your computer operates smoothly and is safeguarded against unnecessary clutter.Main Features:
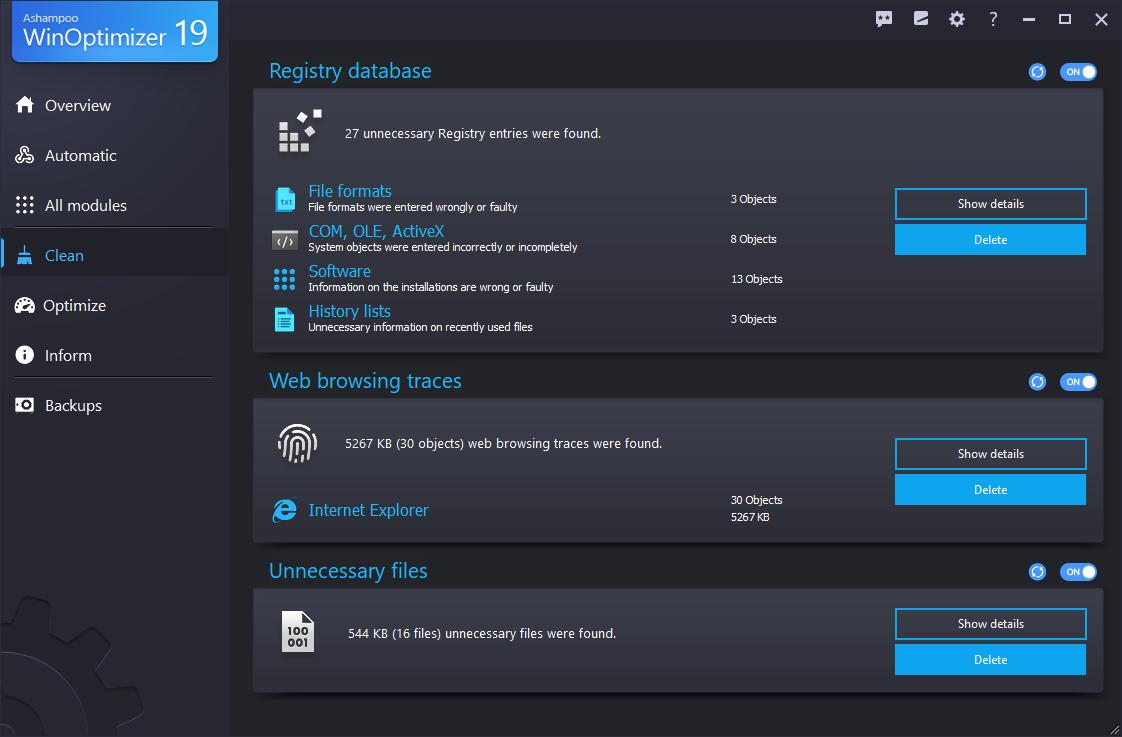
- Cleaning: Efficiently search for and eliminate duplicate files and problematic registry entries to free up valuable disk space.
- Setup: Adjust and optimize system values to boost your computer's performance levels significantly.
- File Management: Seamlessly divide, merge, encrypt or destruct files, catering to all your file handling needs.
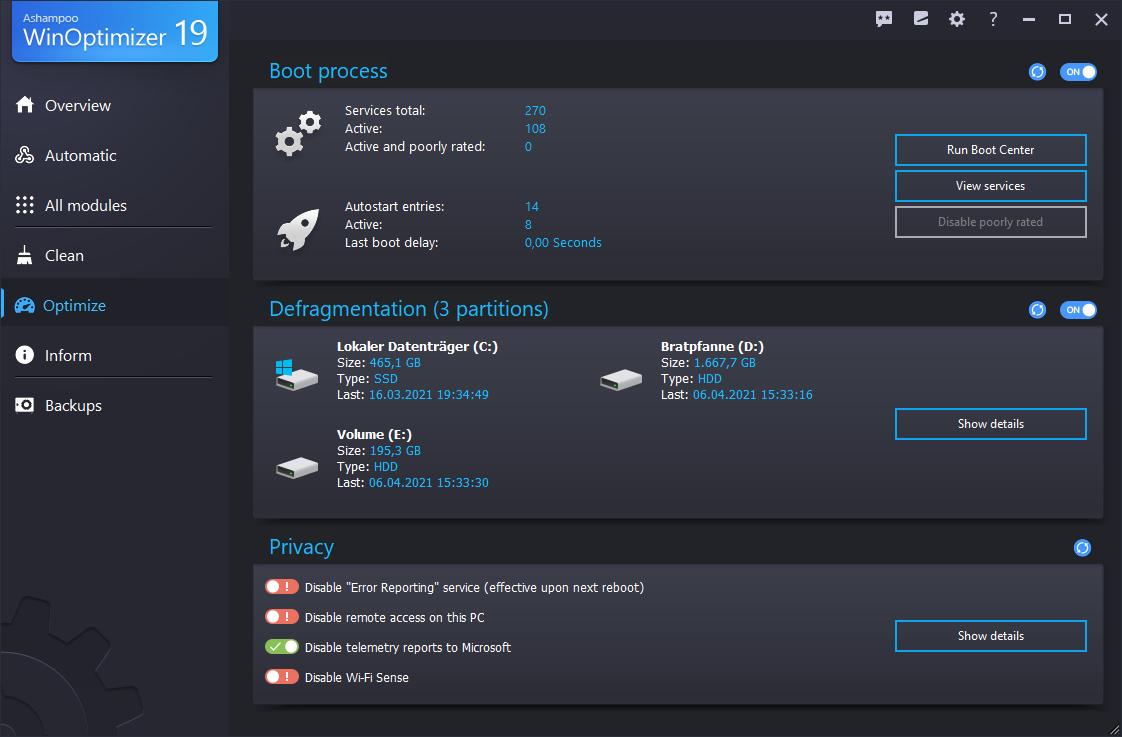
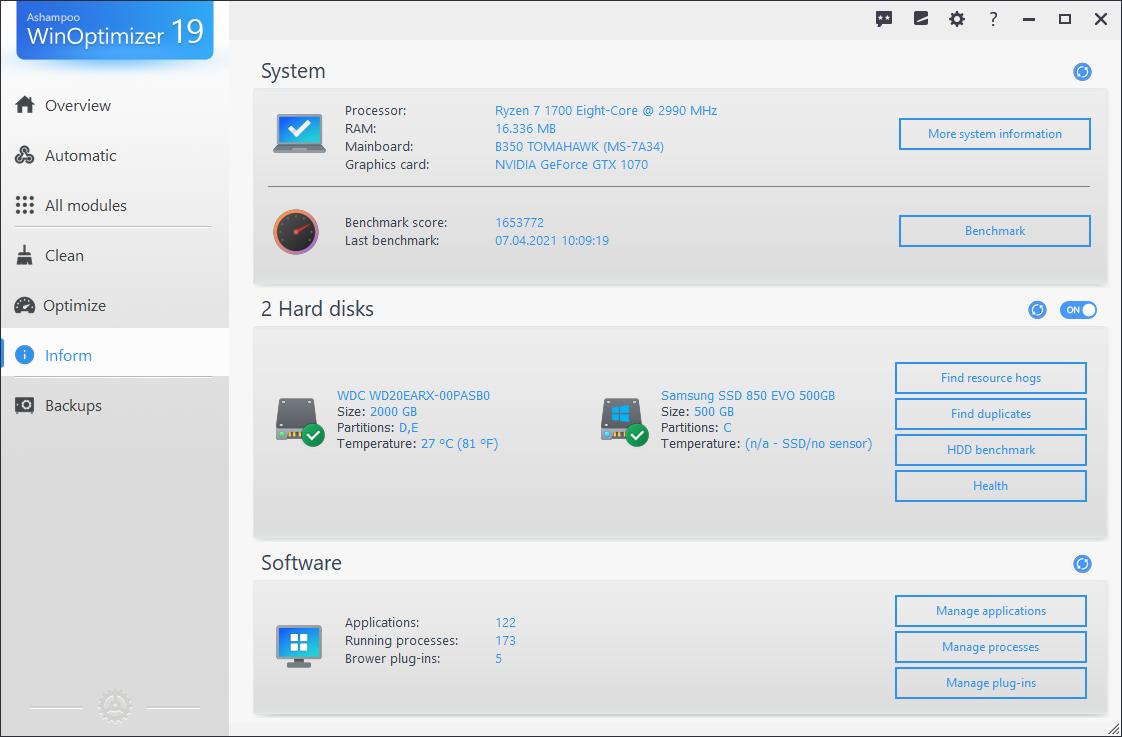
- Windows Setup: Defragment your hard drive and enhance system information retrieval, ensuring optimal system operation.
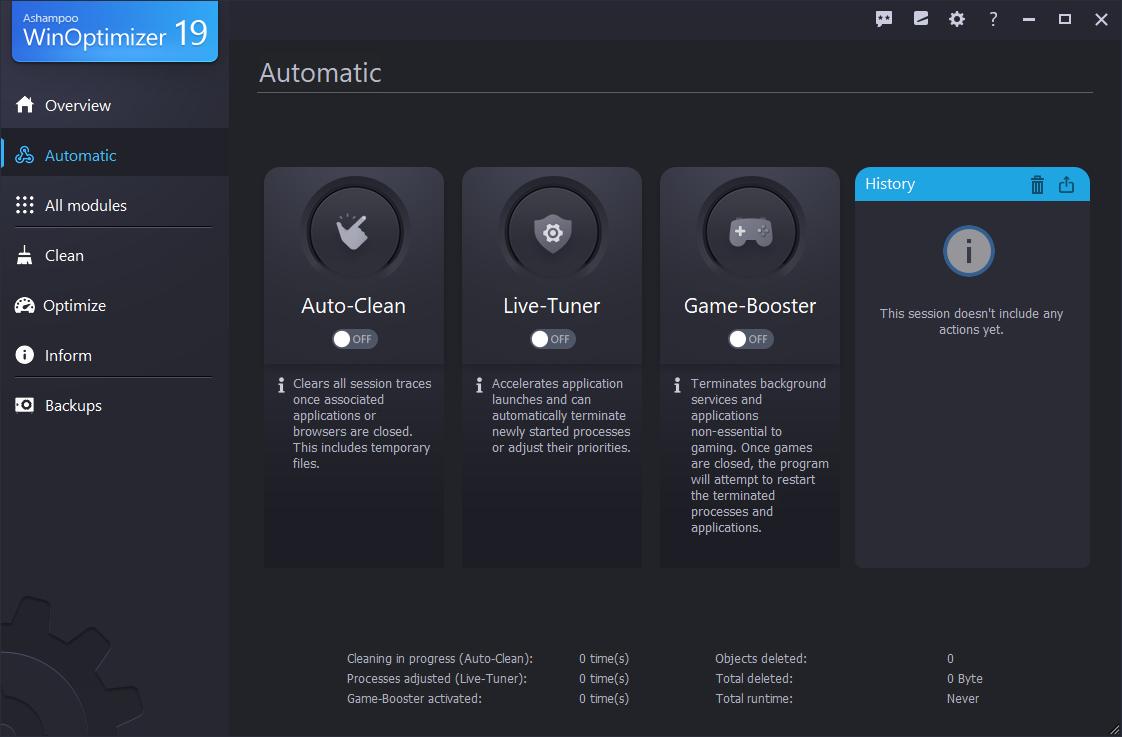
- One-Click Optimization: Simplify your management tasks with a single click for an instant performance boost.
Customization:
Users can personalize their experience by configuring optimization settings to match their specific needs. Ashampoo WinOptimizer allows you to set preferences for cleaning tasks, file management, and system adjustments, making it adaptable to individual workflows.Modes/Functionality:
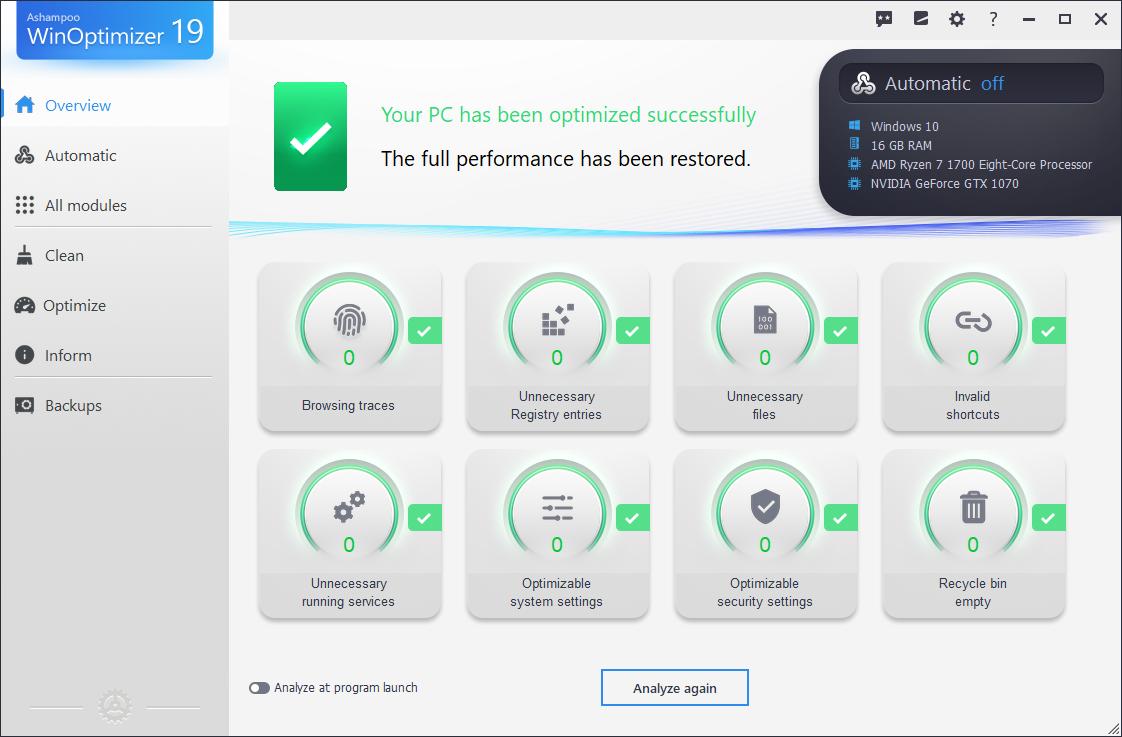
- One-Click Optimization: Quickly optimize your system with a single click, perfect for users who want fast results.
- Advanced Cleaning: Dive deeper into cleaning options to target specific files and registry entries that slow down your system.
- File Manipulation: Take control of your files through advanced options such as encryption and deletion, ensuring your sensitive information remains secure.
Pros and Cons:
Pros:
- User-friendly interface that is easy to navigate.
- Comprehensive cleaning and optimization tools that significantly improve system performance.
- Flexibility in customization options for a tailored experience.
- One-click optimization feature saves time and effort.
Cons:
- Some advanced users may find certain features to be basic.
- Periodic updates are necessary to maintain optimal performance.
Discover more apps
MagiKart: Retro Kart Racing lets you race as various characters, using customizable controls and special items, evoking nostalgia reminiscent of Super Mario Kart.
LunaProxy offers stable residential proxies for social media, with 200 million devices, dynamic pricing, 99.9% uptime, easy API integration, and a profitable affiliate program.
Genius DLL is an easy-to-use application for quickly downloading and registering DLLs, requiring just a few clicks to search, download, and manage libraries.
The Quick Start tab in Google Chrome provides access to installed apps, including a shortcut for iCloud Reminders, enhancing user convenience despite being unofficial.
Tiger Password Recovery is a user-friendly tool that efficiently retrieves lost passwords across various applications and devices using advanced algorithms.
Desktop Gadgets Revived restores classic Windows desktop gadgets, allowing customization with functional and aesthetic widgets on modern operating systems, maintaining compatibility and nostalgic design.
Advanced BAT to EXE Converter transforms BAT files into EXE format, enhancing application protection and aesthetics while allowing versioning and password features for developers.
Renee File Protector is a tool that easily hides and locks files on your computer or external devices, ensuring sensitive information remains secure.